Enforce MFA
You can enforce multi-factor authentication in one of two models:
- Strict, where secured operations always require the highest Authenticator Assurance Level (AAL).
- Lax, where the secured operations require only the
aal1Authenticator Assurance Level (AAL).
You can set the required authentication model for these operations/endpoints:
- User sign-in (getting an Ory Session) /
/sessions/whoamiendpoint - Self-service user settings
Configuration
Follow these steps to enforce multi-factor authentication:
Ory Console
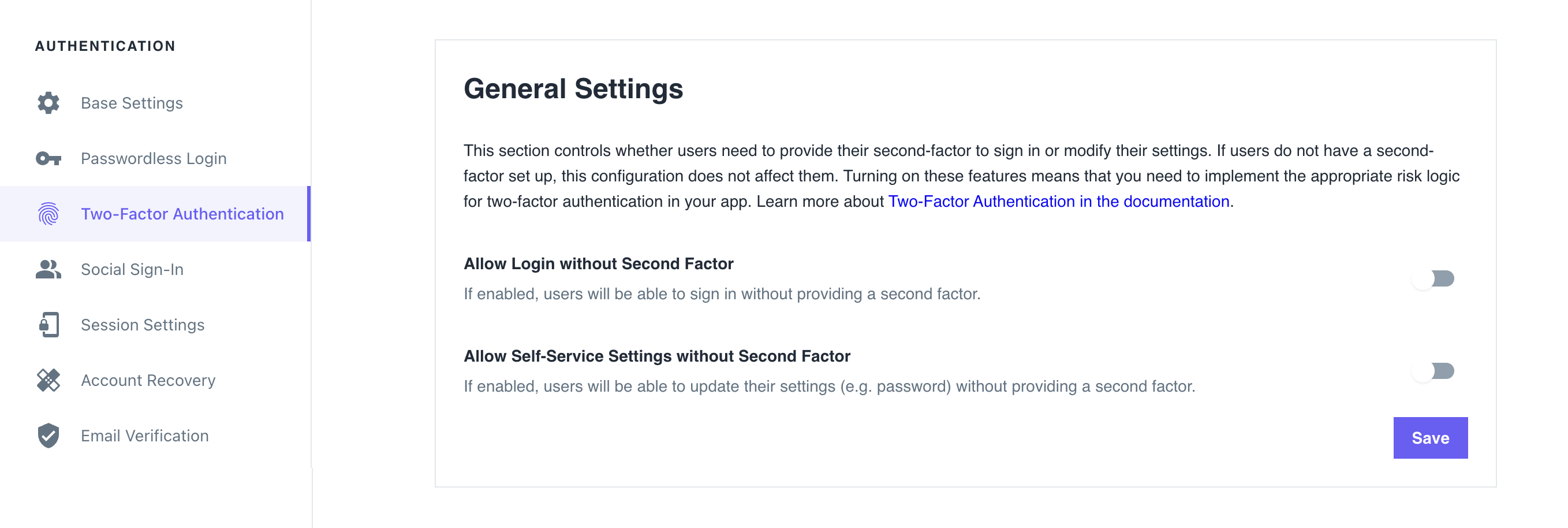
In The Ory Network, the default multi-factor authentication enforcement model is Strict.
To change it to Lax and allow users to sign in or access user settings without authenticating with the second factor, go to the Ory Console → Two-Factor Authentication and use the switches in the General Settings section.
Ory CLI
Follow these steps to adjust the settings in The Ory Network using the Ory CLI:
Get the Ory Identities configuration from your project and save it to a file:
## List all available projects
ory list projects
## Get config
ory get identity-config <project-id> --format yaml > identity-config.yamlAdjust the values of the indicated keys to the desired values:
identity-config.yaml# ...
selfservice:
flows:
settings:
required_aal: aal1
# ...
session:
whoami:
required_aal: aal1
# ...tipUse
aal1for the Lax model andhighest_availablefor the Strict model.Update the Ory Identities configuration using the file you worked with:
ory update identity-config <project-id> --file identity-config.yaml
Self-hosted instances
When working with self-hosted instances of the Ory Identities (Kratos), change the enforcement model by adjusting these keys in the configuration file:
# ...
selfservice:
flows:
settings:
required_aal: aal1
# ...
session:
whoami:
required_aal: highest_available
# ...